Generate Immediate Investigative Leads with a Proven Tool Used by 2,500 Agencies
#1 search engine and advanced analytics fueled by the largest network of police agency data in the United States
REQUEST A CONSULTATIONTHE CHALLENGE FOR LAW ENFORCEMENT
86%
of agencies with staffing shortage in the U.S. (in 2020)
Source: National Police Foundation
With law enforcement agencies across the U.S. grappling with budget cuts, reduced staffing and nationwide scrutiny, there’s perhaps never been a more challenging time to work in policing. On top of all of this, many departments are also facing the ramifications of siloed data and aging technology. At a time when expediency and efficiency are more important than ever before, many agencies lack the software they need to keep up with the pace of change.
IMPROVE EFFICIENCY AND EFFECTIVENESS
CrimeTracer (formerly COPLINK X) is a powerful law enforcement search engine and information platform that enables law enforcement to search data from agencies across the U.S. using natural language speech terms and concepts. With CrimeTracer, officers have instant access to information they need, enabling them to strike the right balance between crime reduction, community engagement, and personal safety.
Create case momentum with immediate tactical leads from a law enforcement search engine that supports more than 30 data sources.
Access over 1.3 billion records from RMS, CAD, LPRs, ShotSpotter, JMS, Court, Warrant Records, and more – from your agency and nearby jurisdictions.
Accelerate investigations with advanced analytics and visualizations to identify offenders in near real-time, keeping your community safe.
Enhance situational awareness even during routine traffic stops to help ensure the best and safest outcome.
Connect to CrimeTracer from any centrally managed device and across all compliant networks.
Control data access and data sharing with the fully CJIS-compliant platform.
-
1. Search through all structured and unstructured data to obtain immediate tactical leads.
-
2. Access more than one billion law enforcement data records from a centralized interface.
-
3. Leverage advanced link analysis to quickly detect relationships between people, places, and events.
-
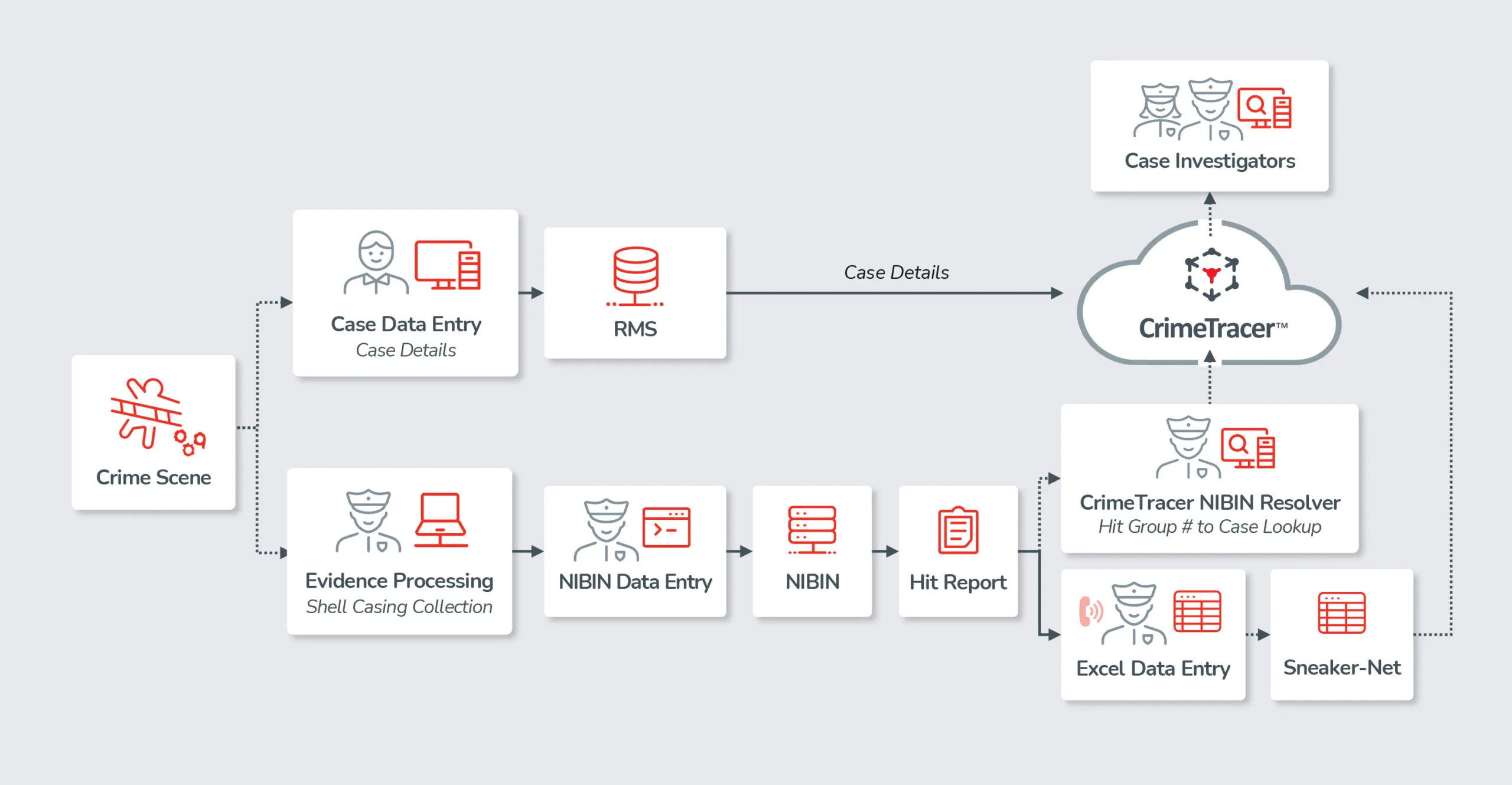
4. Link NIBIN leads to reports, suspects, and other entities.
-
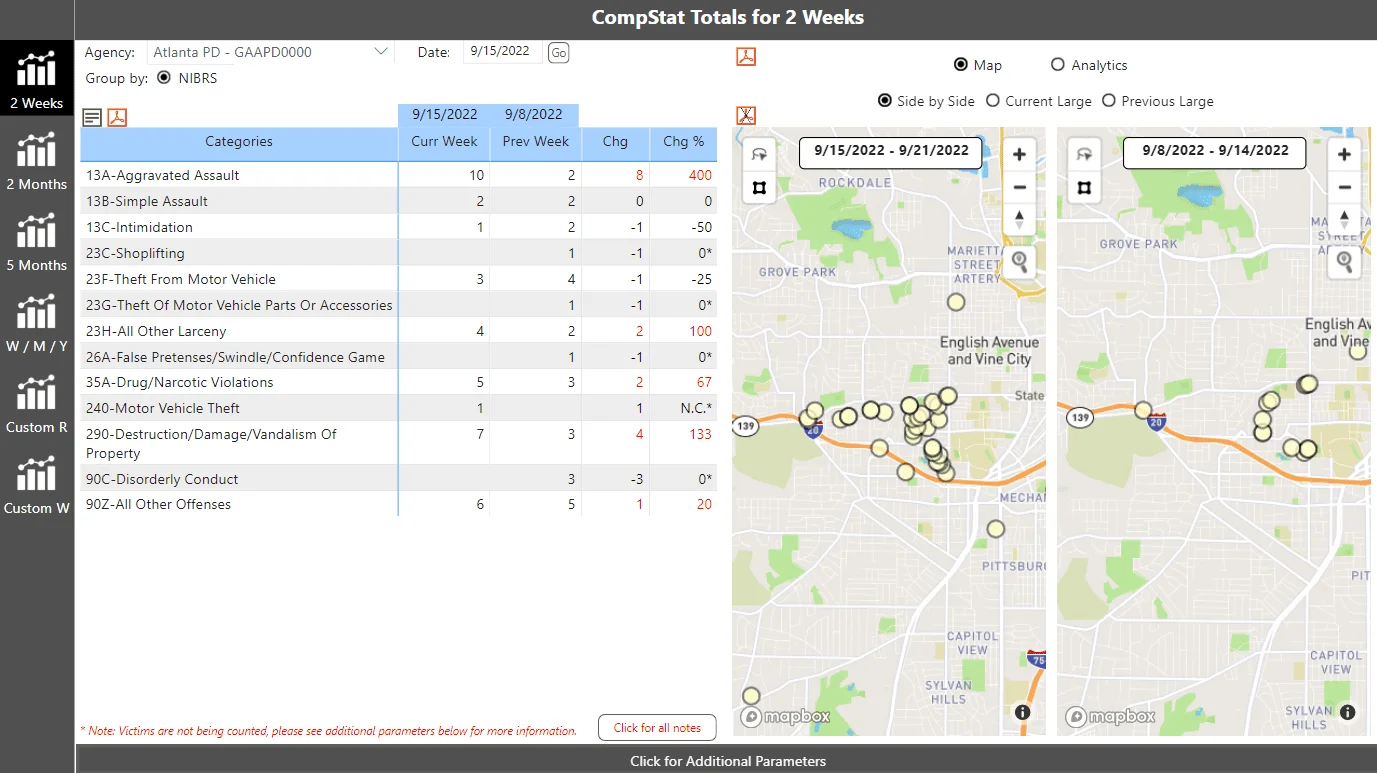
5. Identify crime trends using CompStat to make operational and resource decisions.
-
6. Import CrimeTracer leads into CaseBuilder with one click.
-
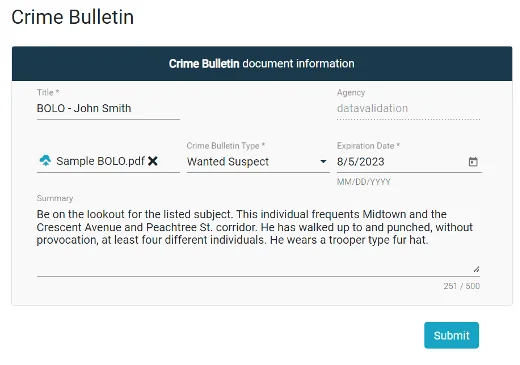
7. Upload time sensitive crime bulletins such as BOLOs for nationwide dissemination.

“With [CrimeTracer], our patrol officers weren’t just responding and reporting, they were actually solving, and the arrests of those violent offenders began really putting a huge dent in our violent crime rates.”
CUSTOMER TESTIMONIALS

Without the information provided by [CrimeTracer], I would have never figured out who committed these robberies since the suspects wore gloves and completely covered their faces. The information I obtained from [CrimeTracer] allowed me to compare more details about the suspects, obtain cellular data and social media information ultimately leading to substantial evidence of the crime. This led to a tri-county take down of all three suspects who are now in custody. Thank you to everyone at [CrimeTracer] for making this system work so well and keep pushing forward to get every agency on board with this system!

Forensic Logic* allowed us to deploy a whole new kind of policing: faster, more agile, more effective, and far more data-driven.

Forensic Logic* is absolutely instrumental in nearly every case we prosecute… What they have built, the power of their technology, it makes your head spin.

Using the limited information available, a quick and simple association search in [CrimeTracer] allowed the Department to quickly focus the investigation. This resulted in the issuance of an arrest warrant for a very violent criminal. [CrimeTracer] is an essential investigative tool, providing our officers with the means to find vital investigative leads that would not otherwise be readily apparent.

The results from the [CrimeTracer] search led to the positive identification of the suspect. I was also able to track the suspect and when he traveled back to San Francisco, he was arrested and is now awaiting trial for murder. Without the information obtained from [CrimeTracer], I would not have known the suspect's whereabouts.
CRIMETRACER PARTNERS



CrimeTracer FAQs
SoundThinking offers:
- ShotSpotter®, an innovative gunshot detection technology that enables law enforcement to proactively address gun violence and arrive at a scene within minutes, saving lives and building community trust in the process.
- CaseBuilder™, a smarter investigation management platform that enables investigative teams to efficiently organize and store case information, track and prioritize assignments, optimize resources, submit materials to prosecution, and more.
- CaseBuilder™ Crime Gun, the first-of-its-kind gun crime tracking and analysis case management tool that enables agencies to better capture, track, prioritize, analyze, and collaborate on incidents that involve firearms.
- ResourceRouter™, a resource management tool that automates the planning of directed patrols and provides transparency around engagement activities.